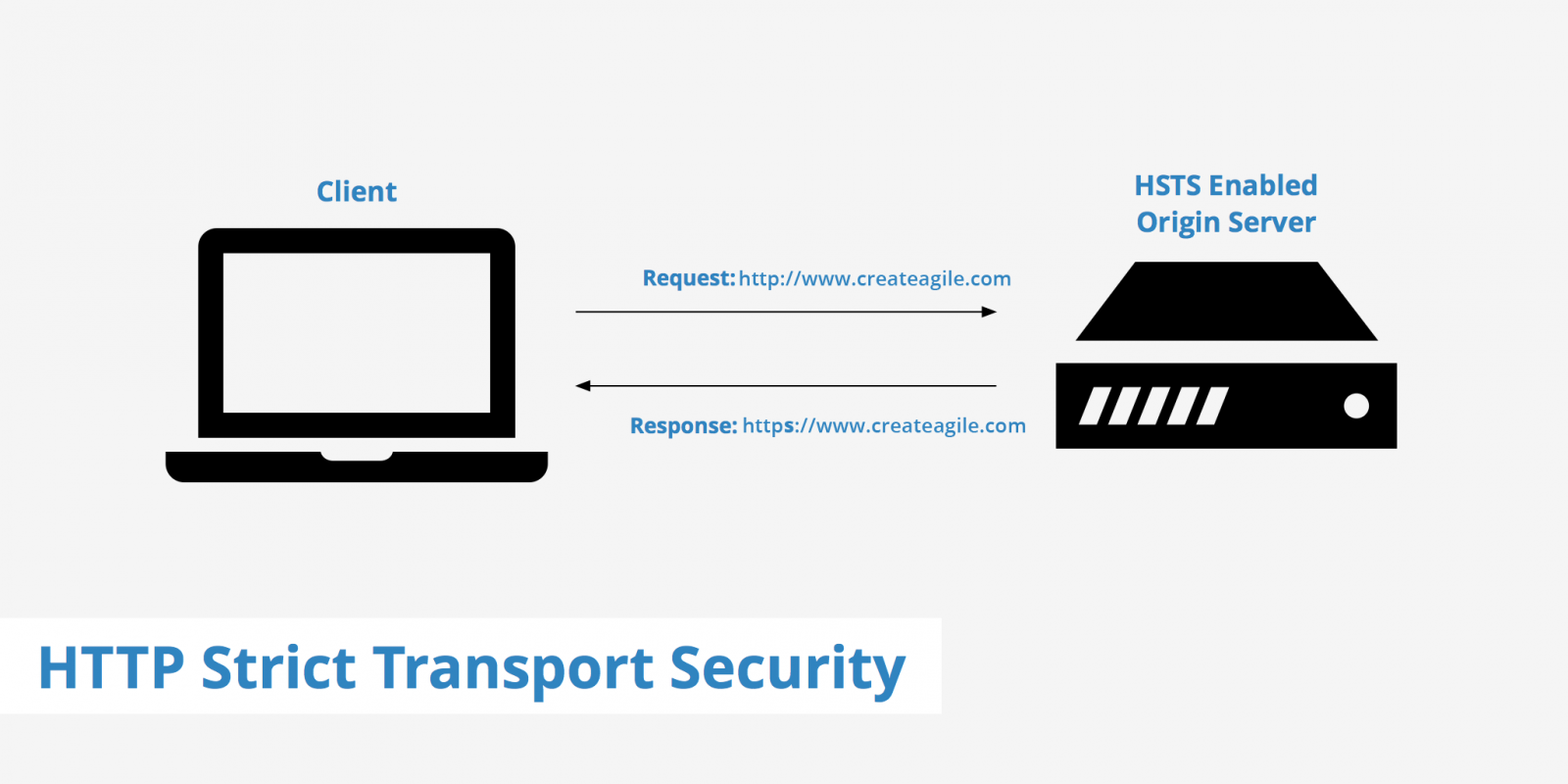
ABOUT HSTS
HTTP Strict Transport Security (HSTS) instructs web browsers to only use secure connections (https://) for all future requests when communicating with a web site. Doing so helps prevent SSL protocol attacks, SSL stripping, cookie hijacking, and other attempts to circumvent SSL protection.
To enable HSTS for your site, you must have a valid SSL certificate already installed and activated. If you do not, and you enable HSTS anyway, visitors will be unable to access your site.
ENABLING HSTS ON LINUX
To enable HSTS for your site, follow these steps:
- Using SSH, the cPanel File Manager, or the Plesk File Manager, navigate to the document root of your site.
- Use your preferred text editor to open the .htaccess file.If the .htaccess file does not already exist, create it.
- Copy the following line, and then paste it into the .htaccess file:
Header set Strict-Transport-Security "max-age=31536000" env=HTTPS
- Save your changes to the .htaccess file. HSTS is now enabled for your site.
When the web server sends this header, any browser that accesses the site over HTTPS will be unable to access the unsecured HTTP site for the specified length of time (in this case, 31,536,000 seconds, or one year). Therefore, as soon as you enable HSTS, you should not stop using SSL on your site. If you do, returning visitors will be unable to access your site.
ENABLING HSTS ON WINDOWS
To enable HSTS for your site, follow these steps:
- Using the Plesk File Manager, navigate to the document root of your site.
- Click the web.config file to open it in the file editor.
- There is a specific location to enter the settings for HSTS, and it is different depending on the existing contents of the web.config file. Please carefully review each of the three scenarios below, and then select the correct one for your situation:
- If the web.config file is empty, paste the entire code below into the editor and click Apply:
<?xml version="1.0" encoding="UTF-8"?> <configuration> <system.webServer> <rewrite> <rules> <rule name="HTTP to HTTPS redirect" stopProcessing="true"> <match url=".*" /> <conditions> <add input="{HTTPS}" pattern="off" ignoreCase="true" /> </conditions> <action type="Redirect" url="https://{HTTP_HOST}{REQUEST_URI}" redirectType="Permanent" /> </rule> </rules> <outboundRules> <rule name="Add Strict-Transport-Security when HTTPS" enabled="true"> <match serverVariable="RESPONSE_Strict_Transport_Security" pattern=".*" /> <conditions> <add input="{HTTPS}" pattern="on" ignoreCase="true" /> </conditions> <action type="Rewrite" value="max-age=31536000; includeSubDomains; preload" /> </rule> </outboundRules> </rewrite> </system.webServer> </configuration> - If the web.config file is not empty, look for the
section. if there is no <?xml version="1.0" encoding="UTF-8"?> <configuration> <other items> </other items> <system.webServer> <rewrite> <rules> <rule name="HTTP to HTTPS redirect" stopProcessing="true"> <match url=".*" /> <conditions> <add input="{HTTPS}" pattern="off" ignoreCase="true" /> </conditions> <action type="Redirect" url="https://{HTTP_HOST}{REQUEST_URI}" redirectType="Permanent" /> </rule> </rules> <outboundRules> <rule name="Add Strict-Transport-Security when HTTPS" enabled="true"> <match serverVariable="RESPONSE_Strict_Transport_Security" pattern=".*" /> <conditions> <add input="{HTTPS}" pattern="on" ignoreCase="true" /> </conditions> <action type="Rewrite" value="max-age=31536000; includeSubDomains; preload" /> </rule> </outboundRules> </rewrite> </system.webServer> </configuration> - Finally, if the web.config file is not empty, and there is a
section, paste in the highlighted red code as shown: <?xml version="1.0" encoding="UTF-8"?> <configuration> <other items> </other items> <system.webServer> <other items> </other items> <rewrite> <rules> <rule name="HTTP to HTTPS redirect" stopProcessing="true"> <match url=".*" /> <conditions> <add input="{HTTPS}" pattern="off" ignoreCase="true" /> </conditions> <action type="Redirect" url="https://{HTTP_HOST}{REQUEST_URI}" redirectType="Permanent" /> </rule> </rules> <outboundRules> <rule name="Add Strict-Transport-Security when HTTPS" enabled="true"> <match serverVariable="RESPONSE_Strict_Transport_Security" pattern=".*" /> <conditions> <add input="{HTTPS}" pattern="on" ignoreCase="true" /> </conditions> <action type="Rewrite" value="max-age=31536000; includeSubDomains; preload" /> </rule> </outboundRules> </rewrite> </system.webServer> </configuration>
- If the web.config file is empty, paste the entire code below into the editor and click Apply:
MORE INFORMATION
For more information about HSTS, please visit https://en.wikipedia.org/wiki/HTTP_Strict_Transport_Security.
Need help? We’re here to help you do your thing.
Email us at hello@createagile.com.